Securing Your Site: Obtain an SSL Certificate with Let’s Encrypt When Your ISP Blocks Port 80
Wildcard certificates are highly beneficial because they secure all subdomains of your main domain with a single certificate. This simplifies domain management by eliminating the need to handle individual certificates for each subdomain.
I chose the DNS-01 challenge for validation for my homelab setup because my Internet Service Provider (ISP) blocks port 80, which is necessary for the HTTP-01 challenge. If your ISP imposes similar restrictions, the DNS-01 challenge might be your best option for obtaining an SSL certificate from Let's Encrypt.
Setting Up
First, I created a directory to store the Let's Encrypt logs:
sudo mkdir /var/log/letsencrypt/
Then, I installed Certbot, which simplifies the SSL certificate issuance and management process:
sudo apt install certbot
To initiate the certificate request, I ran the following command:
certbot certonly --manual
During this setup, Certbot prompted me for an email address for important notifications and to agree to the Let's Encrypt Terms of Service.
youremail@example.com
Once that was done, I entered my domain name in the following format to request a wildcard certificate:
*.yourdomain.com
DNS-01 Challenge Configuration
For the DNS-01 challenge, Certbot provided me with a specific TXT record that needed to be added to my domain's DNS settings under the name:
_acme-challenge
The record value looked something like this:
o7mU8KwvI7A1_phmxzrHOIA9jaGSOjkI-ngCRbSdhpc
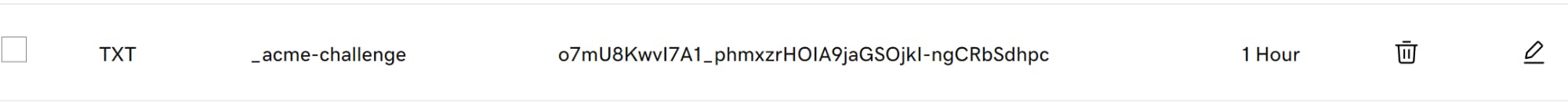
It's crucial NOT to proceed with the SSL setup until this TXT record has fully propagated across DNS servers worldwide. Depending on your DNS provider, this propagation process can take anywhere from a few minutes to an hour. If you proceed too early, you will have to repeat this process.
Check DNS Propagation - Version 1
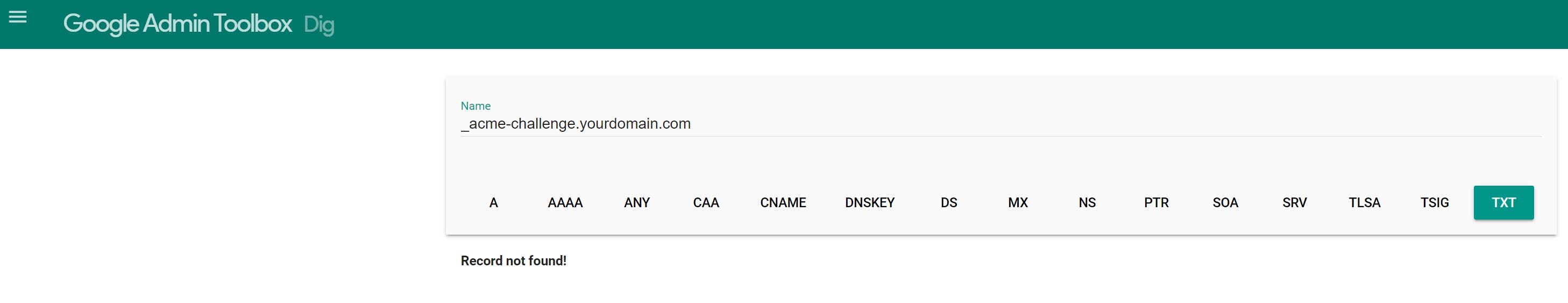
To check if the record has propagated, you can use online tools like the Google Admin Toolbox.
Search for your TXT record under _acme-challenge.yourdomain.com and verify that the record's value matches what you added.
Check DNS Propagation - Version 2
Use this command to test for it propagated:
dig -t txt _acme-challenge.yourdomain.com
Output of this command:
;; ANSWER SECTION:
_acme-challenge.yourdomain.com. 0 IN TXT "AxSzdAxR3yyJYok3KkuIRwod82Ld5MhYuH4oJ8"
Certificate Renewal
- Open the crontab for editing:
sudo crontab -e
- Add a line to the crontab file to schedule the task. Here, the renewal process is set to run twice daily, which is frequent enough to handle any potential issues well before the certificate's expiration. The exact timing (4:47 AM and PM in this example) is staggered to avoid peak times on Let's Encrypt's servers. When you use the
--post-hookoption with Certbot, it ensures that the specified command, such as restarting or reloading Nginx, only runs after a successful renewal of the certificate. This is a safeguard to prevent service disruptions in case the renewal process encounters an issue.
certbot renew --quiet --post-hook "systemctl reload nginx"
Conclusion
Dealing with an ISP that blocks port 80 can make securing your website with an SSL certificate a bit tricky. The DNS-01 challenge comes to the rescue, providing a workaround for this hiccup. Just follow these steps, and you'll be able to get and handle an SSL certificate from Let's Encrypt without the need for port 80.